- 1password Github 2fa Free
- Github Enable 2fa
- 1password Github 2fa Plugin
- Github 2fa Cli
- 1password Github 2fa Tutorial
- 1password Github 2fa Code
For a long time, I was reluctant about using a password manager. One of the advantages of using one is the ability to have a strong and unique password for each service, without having to memorize each password. It drastically improves security.
Without a password manager, we unavoidably start reusing (bad) passwords across several services. Sometimes those services get hacked, and our info gets leaked, and you already know how this story ends.
A password manager nicely addresses those problems, but it also introduces new issues. Now, the reason why I was reluctant to use one was twofold:
- Trusting a third-party with all my passwords;
- Being unable to log in a specific service because I don’t have access to my password manager app.
Mar 25, 2020 I currently use LastPass to manage my passwords, but I am going to switch to 1Password soon. I decided to use Bitwarden as well but solely for TOTP codes. 1Password can also handle TOTP codes, but I am willing to deal with the hassle of having two password managers to avoid using the same service for both passwords and 2FA. Bitwarden, the open source password manager, makes it easy to generate and store unique passwords for any browser or device. Create your free account on the platform with end-to-end encryption and flexible integration options for you or your business.
The second reason is also why I use two-factor authentication very selectively — only on services that offer a reliable recovery method and/or are critical for me. And by a reliable method I mean one-time recovery codes. Using SMS as a recovery method is not always the best option for me because I travel abroad quite frequently nowadays and I can’t count on being able to receive SMS.
Sure, I can always reset my password and change it temporarily in case I don’t have access to my password manager (as long as I have access to my email account).
But it would also be annoying if I wanted to access something on my mobile phone for instance, and having to type a long random string doesn’t sound very fun. So it would be good to have a mobile app to sync my passwords across my devices.
Having passwords stored in a cloud server weaken a lot the security factor of such services. Even though my info will be encrypted using industry standards (well, at least I have to trust they are doing their best), that means my passwords will be stored in an external storage and will probably be jumping around other servers in multiple backups and so on.
A chain is only as strong as its weakest link.
Even having the best technologies, the most secure servers, and strongest security features, none of this really matters if you don’t trust the company behind the service. Social engineering is known to be one of the most effective security attacks. There are many examples out there, for example when an attacker used social engineering to trick a Namecheap support employee to gain access to an account protected by two-factor authentication.
You also need to trust on their processes and personnel.
This year, when Troy Hunt announced the partnership between 1Password and haveibeenpwned.com, I thought about giving it a shot. I’ve been using it since then, and I never looked back.
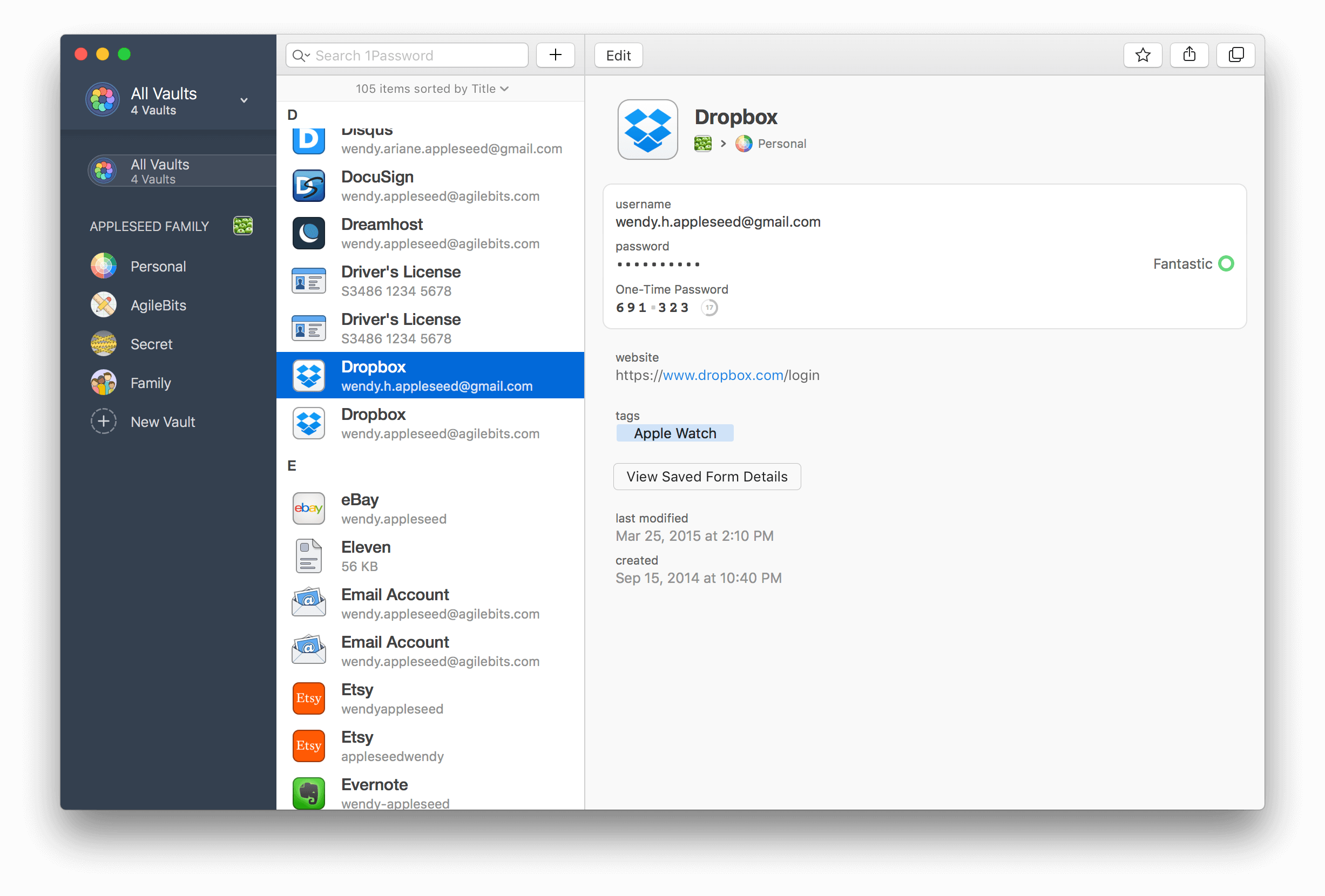
1Password is such a great product, and it still amazes me how much thought they put into some of its features. For me, the best thing about 1Password is the browser plugins, so you can log in just by hitting the shortcut ⌘ + . This is so convenient and just works.
The second best thing is the ability to have 2FA stored inside my 1Password vault:
This is awesome because if I lose my phone, I don’t need to set up all my 2FA again or go through all recovery process. Also, the workflow is so smooth. After you hit ⌘ + to log in, it will automatically copy the one-time password to your clipboard, so you simply press ⌘ + V after that to complete the authentication. After you are logged in, it will automatically restore your clipboard with whatever was there.
Another cool thing about it is that you can store secure notes, credit card pin code, software licenses, and serial keys.
To be fair, I don’t trust all my stuff there. Especially my main email accounts that are used to register to other services. For those, I keep unique passwords stored only on my mind. That way, even if I lose my recovery key from 1Password, I’m still able to regain access to the software and services that I use. But other than that, it’s been my standard way of storing sensitive information.
Latest versionReleased:
A Python client and wrapper around the 1Password CLI.
Project description
Python wrapper around 1Password password manager for usage within python scripts andJupyter Notebooks. Developed by Data Scientists from Wandera to be used within bothresearch and python services use cases.
Installation
If you have issues with PyYaml or other distutils installed packages then use:
Both of these will install the op cli and python client.This is currently fixed at op version 1.8.0 to ensure compatibility. If you wish to use a higher version of op youcan by running op update in a terminal however note that we cannot ensure it will work with our client yet.
Mac OS users will be prompted with a seperate installation windows to ensure you have a signed version of op - makesure to check other desktops that the installer might pop up on.
1password Github 2fa Free
Basic Usage
Currently tested on Mac OS and Linux.
On first usage users will be asked for both the enrolled email, secret key and masterpassword. There is also verification of your account domain and name.
For all following usages you will only be asked for a master password.
You will be given 3 attempts and then pointed to reset password documentation or alternatively you canrestart your kernel.
No passwords are stored in memory without encryption.
If you have 2FA turned on for your 1Password account the client will ask for your six digit authenticator code.
Input formats
To be sure what you are using is of the right format
- Enrolled email: standard email format e.g. user@example.com
- Secret key: provided by 1Password e.g. ##-######-######-#####-#####-#####-#####
- Account domain: domain that you would login to 1Password via browser e.g. example.1password.com
- Account name: subdomain or account name that cli can use for multiple account holders e.g. example
Contributing
The travis build will run with any PR or commit to master branch and then updatesthe master branch with a new minor version for contributors to branch from.
This means when contributing you should create a feature branch off of the master branch and withoutmanually bumping the version can focus on development. Merge back into master.
Later admins will bump major versions.
CLI coverage
Full op documentation can be found here: https://support.1password.com/command-line-reference/
The below is correct as of version 0.3.0.
Commands
This is the set of commands the current python SDK covers:
- create: Create an object
- document
- delete: Remove an object
- item: we use this method to remove documents but now there is a new delete document method
- get: Get details about an object
- document
- item
- list: List objects and events
- items
- vaults
- signin: Sign in to a 1Password account
- signout: Sign out of a 1Password account
This is what still needs developing due to new functionality being released:
- add: Grant access to groups or vaults
- group
- user
- completion: Generate shell completion information
- confirm: Confirm a user
- create: Create an object
- group
- user
- item
- vault
- delete: Remove an object
- document
- user
- vault
- group
- trash
- edit: Edit an object
- document
- group
- item
- user
- vault
- encode: Encode the JSON needed to create an item
- forget: Remove a 1Password account from this device
- get: Get details about an object
- account
- group
- template
- totp
- user
- vault
- list: List objects and events
- documents
- events
- groups
- templates
- users
- reactivate: Reactivate a suspended user
- remove: Revoke access to groups or vaults
- suspend: Suspend a user
- update: Check for and download updates
Roadmap
- Add Windows functionality
- Add clean uninstall of client and op
- Remove subprocess usage everywhere -> use pexpect
- Add test docker image
- Get full UT coverage
- Align response types into JSON / lists instead of JSON strings
- Ensure full and matching functionality of CLI in python
- add
- confirm
- create
- delete
- edit
- encode
- forget
- get
- list
- reactivate
- remove
- suspend
- Use the new CLI update method
Release historyRelease notifications | RSS feed
0.5.1
0.5.0
0.4.5
0.4.4
0.4.3
0.4.2
0.4.1
0.4.0
0.3.0
0.2.5
0.2.4
0.2.3
0.2.2
0.2.1
0.2.0
0.1.9
0.1.8
0.1.7
0.1.6
0.1.5
Github Enable 2fa
0.1.4
1password Github 2fa Plugin
0.1.3
Github 2fa Cli
0.1.2
0.1.1
0.1.0
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
| Filename, size | File type | Python version | Upload date | Hashes |
|---|---|---|---|---|
| Filename, size 1password-0.5.1.tar.gz (11.7 kB) | File type Source | Python version None | Upload date | Hashes |
1password Github 2fa Tutorial
Hashes for 1password-0.5.1.tar.gz
1password Github 2fa Code
| Algorithm | Hash digest |
|---|---|
| SHA256 | e2cc9747b9f703c75ff45d2612d8bc8e9d4e46f0ab03b9a2605271833987a350 |
| MD5 | f9664b861a888241b9203c2fba7aa01e |
| BLAKE2-256 | b926f1040bf5a1665fd8af86f83cecbe2657893c69843f578735ba6d218a24d4 |
